Navigating NIS2: The Next Frontier for Supply Chain Cybersecurity

As the Network and Information Security Directive (NIS2) went live on 17 October 2024, organizations across Europe face an unprecedented challenge. While NIS2 is designed to bolster the cybersecurity of critical infrastructure sectors, its ripple effects will extend well beyond the immediately regulated industries.
From manufacturing to postal and food, supply chains that underpin these industries are equally under threat. Yet for many organizations cybersecurity is still an afterthought in the complex and multi-layered world of supply chain management.
In the second of a four-part series on NIS2, CyXcel’s Technical Director Ngaire Guzzetti discusses the impact of NIS2 on supply chains.

NIS2 has dramatically changed the state of play. Companies and supply chains that fall within the scope of the new regulations are obliged to take proactive steps.
In recent years, supply chains have primarily been defined by two key priorities: efficiency and cost. Businesses have focused on streamlining their operations, reducing production and delivery times, and optimizing procurement processes to maintain profitability in competitive markets.
Cybersecurity of Supply Chains
Cybersecurity, while a growing concern, has traditionally taken a backseat. Many organizations have viewed it as an issue for IT teams to manage or a risk primarily for digital service providers — not something that needs to permeate every layer of the supply chain.
This is an unsustainable and risky mindset. Supply chains today are not just physical networks of goods and services but deeply interconnected digital ecosystems. Every supplier, logistics provider, manufacturer and retailer within the chain is likely using some form of digital technology to track inventory, manage orders and communicate with partners and customers alike.
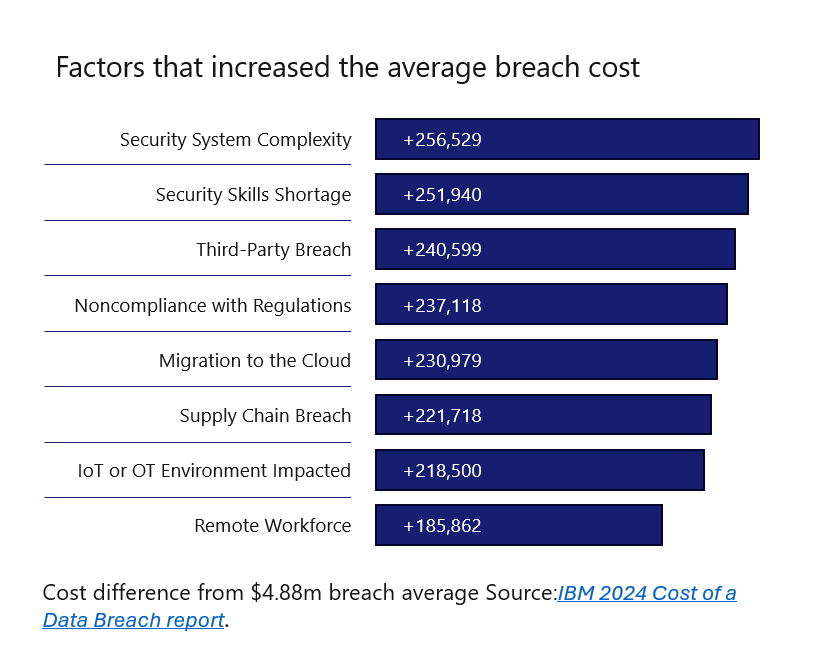
These digital touchpoints are potential vulnerabilities, creating entry points for cyberattacks and leading to very costly results. IBM’s 2024 Cost of a Data Breach Report details how third-party breaches (including supply chain breaches) are in the top three factors for amplified breach costs.
Increasing Technological Dependencies
The reliance on automated systems within manufacturing processes is rising rapidly, often relying on the organization’s main network for operations. Most manufacturers will have implemented stringent fire safety mechanisms, recognizing that a physical fire would shut down manufacturing operations and have a devastating impact on the business.
However, few put the same emphasis on the cybersecurity of these operations, failing to recognize that a cyber incident would have the same, if not worse, impact on the business functions. A cyber incident, malicious or otherwise, could originate from any link in the supply chain, affecting a number of businesses. This makes the implementation of a third-party risk management process (TPRM) critical.
Yet the 2024 UK government statistics show that still only 36% of businesses have undertaken cybersecurity risk assessments in the last year, with only 10% saying they review the risks posed by immediate suppliers. This alone is alarming, without even considering other risks associated with complex supply chains.
Global Impact of Supply Chain Disruptions
Recent high-profile incidents have underlined the gravity of this risk.
A ransomware attack on a relatively small logistics company, for instance, can disrupt operations for countless businesses downstream. In the worst cases, as with KNP Logistics, a ransomware attack resulted in the company’s insolvency, thus forcing customers critically reliant on their services to rapidly find alternatives.
The ripple effect of such attacks can be devastating, with supply chain delays, data breaches and reputational damage impacting companies that had no direct involvement in the initial breach. In other words, when it comes to supply chain security, the weakest link can be just as important as the strongest.
A cyber incident in supply chains can have a global economic impact.
This was apparent in the ransomware attack against US Colonial Pipeline in 2021, and also more recently in July 2024 when an IT outage in CrowdStrike’s systems caused an estimated $10bn worth of damage to the global economy, not to mention the impact of disruptions caused to airline traffic, and most concerningly, delays in delivering medical care to thousands of people, including radiotherapy treatment.
Nevertheless, despite these risks, many organizations still assume that their supply chain is secure:
- Supplier contracts mist mention vague cybersecurity requirements but lack the teeth to enforce compliance.
- Vendor assessments may be infrequent or overlook digital risks entirely.
Trust, for many, is still based on reputation rather than verifiable security practices. It’s a bit like trusting the chef at your favourite restaurant because they’ve been open for years — without noticing they’ve never once cleaned the kitchen
Change in Direction: NIS2
NIS2 has forced a change to that.
The directive significantly broadens the scope of industries covered in NIS1, extending its reach into sectors that previously flew under the regulatory radar, such as postal and courier services, manufacturing, food producers and research organizations (among others).
This means that even businesses that do not consider themselves part of ‘critical infrastructure’ may find themselves indirectly impacted if they supply or partner with a regulated entity. Cybersecurity can no longer be viewed as a distant concern — it's about to become a fundamental part of how supply chains operate.
A recent Gartner press release forecast that by 2025, 45% of organizations globally will have encountered a software supply chain attack. This represents a significant rise in such incidents and a three-fold increase compared to 2021, re-affirming the critical need for legislated obligations.
So, what does the future hold in the age of NIS2? In short: a much more regulated and scrutinized approach to cybersecurity across supply chains.
Enhanced Due Diligence Requirements
The directive imposes stricter requirements for organizations not just to secure their own networks but to ensure that their suppliers and service providers are also adhering to robust cybersecurity practices. This expands the scope of due diligence well beyond immediate vendors and into second- and third-tier suppliers, creating a complex but necessary web of accountability.
In practice, this means that businesses will need to move from reactive to proactive cybersecurity. Rather than assuming that a vendor’s security protocols are adequate, companies will need to actively verify compliance through audits, testing and continuous monitoring.
Supply chains will have to be mapped meticulously, with risk assessments conducted at each level to identify potential vulnerabilities.
NIS2 also emphasizes the need for reporting and information-sharing across sectors, which will further complicate supplier relationships but also improve resilience against attacks.
Cybersecurity as Market Differentiator
Perhaps one of the most profound shifts will be in how organizations prioritize their supplier relationships. Efficiency and cost-effectiveness will remain important, but cybersecurity will now become a deciding factor in who wins a contract.
Suppliers that fail to demonstrate compliance with NIS2 may find themselves cut from the chain, regardless of how affordable or efficient their services may be. This will lead to a restructuring of many supply chains as companies prioritize cybersecurity alongside price and performance.
Impact on SMEs
For small- and medium-sized enterprises (SMEs) in particular, this presents both a challenge and an opportunity:
- Many SMEs do not have the resources or expertise to implement advanced cybersecurity measures on their own, yet NIS2 Will require them to meet the same standards as their larger counterparts.
- On the other hand, SMEs that can adapt quickly and invest in cybersecurity will position themselves as attractive partners in a more security-conscious market.
The future belongs to those who can balance agility with resilience.
Digital Sovereignty and Cyber Resilience
At a more strategic level, NIS2 signals a broader trend toward digital sovereignty and cyber resilience. Governments and businesses alike are recognizing that supply chains are not just about physical goods or digital services — they are also about information.
Protecting that information is just as critical as protecting any physical asset, and companies will need to build systems that are resilient to both digital and physical disruptions. This convergence of digital and physical security is likely to accelerate in the coming years, with cybersecurity becoming an integral part of supply chain resilience.
How Supply Chain Cybersecurity Expertise Can Help You Adapt
The question, then, is not if your supply chain will be affected by NIS2, but how you will respond.
For many organizations, navigating these changes will require more than just a tweak to existing processes: it will demand a fundamental shift in how cybersecurity is integrated into supply chain management. This is where the expertise of a supply chain-focused cybersecurity consultancy, such as CyXcel, becomes invaluable.
1. Knowing Your Supply Chain
The first step for businesses is to gain a comprehensive understanding of their current supply chain security posture. This involves mapping out and tiering all suppliers, assessing their cybersecurity measures and identifying potential points of vulnerability.
External experts can help guide this process, using a risk-based approach to identify which suppliers pose the greatest risk and which are most critical to business continuity. By prioritizing the highest-risk areas, organizations can focus their efforts where they will have the greatest impact.
2. Transitioning to Cyber Resilience
Companies will also need support in developing and implementing robust cybersecurity procedures.
This will require leveraging expertise in both supply chain management and geopolitical risks to cross-border supply chains. Moreover, legal and technical cybersecurity are necessary for crafting tailored cybersecurity requirements for suppliers, building security into contract negotiations, ensuring that both parties are held accountable for compliance, and providing expert legal advice with regard to regulatory compliance.
Companies may also require regular penetration testing, real-time monitoring, and detailed incident response plans — all of which are critical in mitigating the impact of a cyberattack.
3. Staff Training and Institutional Awareness
Training and awareness are also key. Even the most sophisticated security systems can be undone by human error, and NIS2 recognizes this by including specific provisions for employee training.
Regular, customized training programmes for both internal staff and external suppliers are essential for building a culture of security awareness throughout the supply chain. After all, your supply chain is only as strong as its weakest link, and that link is often an untrained employee of a supplier who clicks on a suspicious email.
Protecting your Business
Ultimately, NIS2 is a wake-up call for organizations that have yet to fully integrate cybersecurity into their supply chain management. It is not just about avoiding fines or meeting regulatory requirements — it is about protecting your business (and, in some cases, the global economy) from the very real threats that exist in today’s digital world. By taking proactive steps now, with the guidance of cybersecurity, legal, geopolitical and supply chain experts, companies can turn this challenge into an opportunity for growth, resilience and long-term success.
The road ahead may be complex, but the direction is clear. The future belongs to those who can manage not just the flow of goods, but the flow of information — safely, securely and with confidence.
Photo by Maël BALLAND on Unsplash
The forthcoming articles in this four-part series on NIS2 will take a closer look at the key implications of the new regulation, specifically:
- Incident Reporting Requirements & New Approach to Business Continuity
- Evolution of the Insurance Market
We can help
CyXcel specialises in helping organisations navigate the complex yet critical NIS2 obligations thought tailored risk assessments, robust incident response planning and supply chain governance strategies. We are here to empower your compliance journey and strengthen your cyber defence posture to ensure compliance with NIS2 and securing supply chain resilience.
For more information, or to speak with one of our team about how we can help your business, contact us today.
